31 | Add to Reading ListSource URL: www.waukeshadiversion.orgLanguage: English - Date: 2016-06-21 15:09:27
|
|---|
32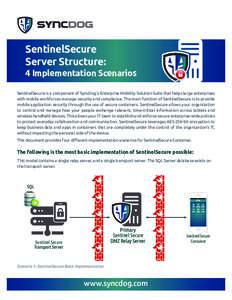 | Add to Reading ListSource URL: www.syncdog.comLanguage: English - Date: 2016-05-16 17:21:11
|
|---|
33 | Add to Reading ListSource URL: www.haproxy.comLanguage: English - Date: 2014-04-28 06:21:22
|
|---|
34 | Add to Reading ListSource URL: www.pwc.chLanguage: English |
|---|
35 | Add to Reading ListSource URL: www.dourish.comLanguage: English - Date: 2008-06-14 12:49:18
|
|---|
36 | Add to Reading ListSource URL: karpinski.orgLanguage: English |
|---|
37 | Add to Reading ListSource URL: cocoa.ethz.chLanguage: English - Date: 2013-07-17 07:17:50
|
|---|
38 | Add to Reading ListSource URL: www.cs.columbia.eduLanguage: English - Date: 2012-10-05 00:01:36
|
|---|
39 | Add to Reading ListSource URL: hcraj.nic.inLanguage: English - Date: 2010-06-21 01:26:02
|
|---|
40 | Add to Reading ListSource URL: www.boydadamson.comLanguage: English - Date: 2013-08-02 08:16:58
|
|---|